How to Know if You Iphone Is Hacked
Contents
- How your phone can be hacked
- How to know if your phone is hacked
- How to know if your phone camera is hacked
- How to observe out who hacked your phone
- How to remove a hacker from my telephone
- Restoring your iPhone using Catalina
- Restoring your Android phone
- How to block hackers from my phone
- Is your phone rubber while turned off?
- Can y'all be hacked with a call?
- Is there an app to see if my phone has been hacked?
- Browsing privately with a VPN
Hackers are ever sharpening their tools. Below nosotros will explain how your phone can exist hacked and how to identify and remove a hacker from your phone.
How your telephone can be hacked
There are many means to hack your telephone. Some don't even require advanced tech knowledge:
- Sim swap attack. By using this assail, hackers can transfer your phone number to their ain SIM card and have over your accounts;
- Spyware that collects your data. Some spy apps are pretty easy to get concur of and can be used past a person without avant-garde IT knowledge. This lets them remotely monitor your phone activities. A person can install such an app by getting a direct access to your device;
- You might get malware via public Wi-Fi networks or charging stations. Hackers tin can gear up fake Wi-Fi networks, called evil twin networks, to redirect you to malicious websites or steal data via USB cable at a charging station;
- Phishing text, Facebook or electronic mail letters with malicious links that install malware and snatch your data;
- You might as well download malware from suspicious sites while downloading apps or by clicking on malicious pop-ups or links.
Try NordVPN, information technology secures public Wi-Fi past encrypting your information traffic.
How to know if your phone is hacked
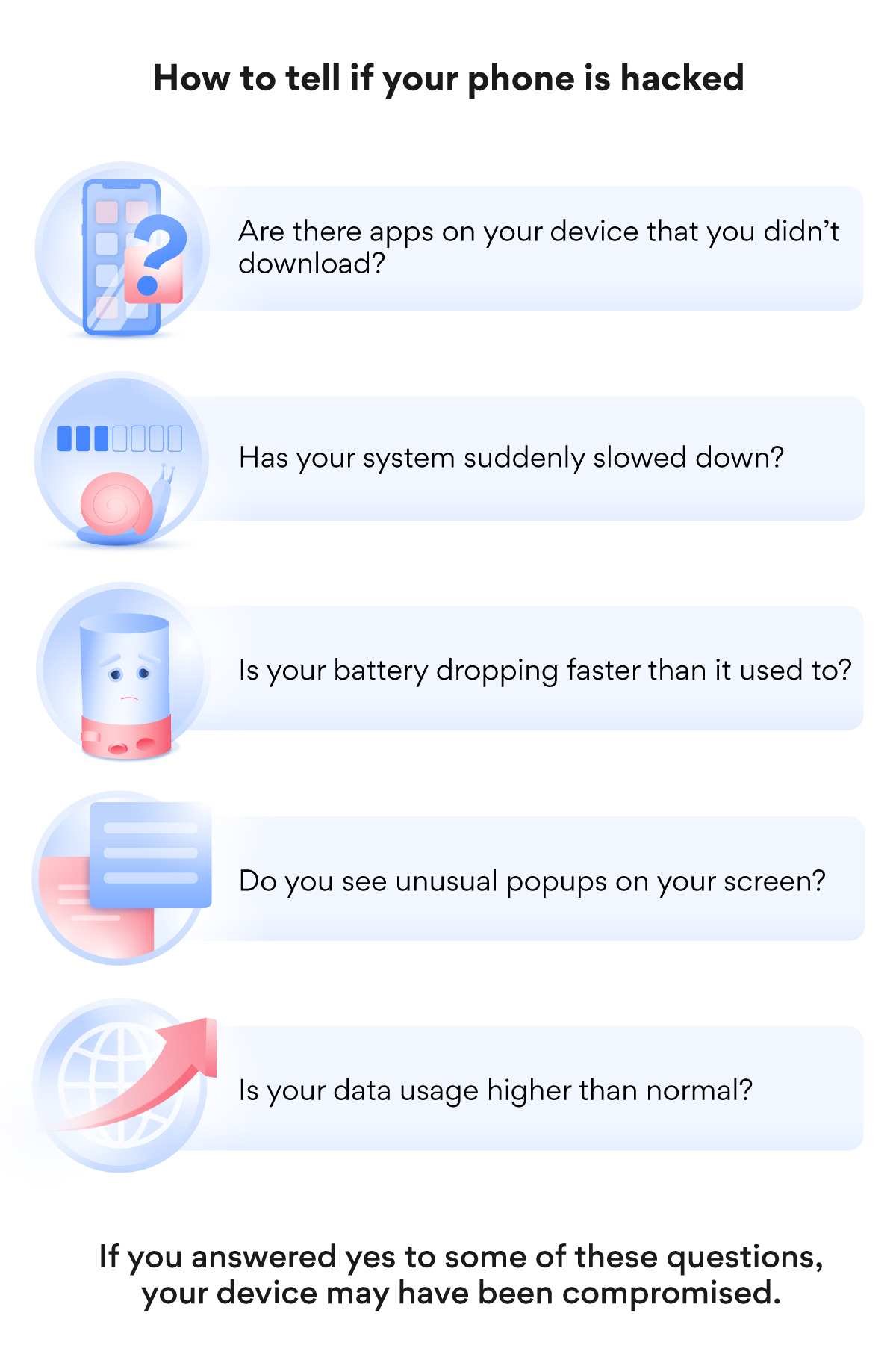
Have you always wondered "Is my telephone hacked?" Here are some signs:
- You notice something you lot don't recognize on your phone (e.g., apps you didn't download, messages you didn't ship, purchases you didn't make, suspicious telephone calls);
- Your phone works wearisome. It uses way more resource and battery power and becomes hotter than usual. Malware working in the background might reduce its power significantly;
- Mysterious data usage spikes without any changes on your function. Malicious processes might be consuming your mobile information in the background as they track what you lot do;
- Foreign behavior. Apps that don't run the way they should, switch on and off unexpectedly, or that crash or fail to load;
- Pop-ups. If you lot notice lots of popular-ups actualization on your screen, you probably accept spyware or malware.
How to know if your telephone camera is hacked
If you lot suspect that your phone camera was hacked, in that location are a few more tell-tale signs that someone else is using information technology remotely. For instance, y'all may notice photos and videos in your gallery that you don't remember taking. Of course, you tin accidentally record something, but if you continue finding new ones, information technology's a sign that someone might accept control over your camera.
The wink lighting upwardly when you're not using your telephone is another affair to look out for. Both the camera and flash demand a lot of resource and bombardment power. Therefore, if someone is remotely controlling your device, you will notice information technology getting very hot fifty-fifty when you don't use information technology.
How to detect out who hacked your telephone
Hackers aren't the only culprits, sometimes an ex-partner, or a suspicious parent who has concrete access to your device, could install a tracking app that secretly tracks your location, messages, and calls.
Endeavor checking all the apps you lot don't recognize and any suspicious phone numbers or social media accounts that have interacted with you. A quick search might find some associations, just tracking hackers usually requires a cybersecurity expert. It'due south usually worth reporting these cases to your local or national law enforcement for further investigation.
Information technology's also worth considering who might take physical access to your phone. If you have a weak password, someone might take guessed it and might have had total access to your device.
How to remove a hacker from my phone
Hither's what to do if your phone has been hacked:
- Change your passwords immediately. You can observe out our tips for stronger passwords here. You tin also use our Nordpass app to store your potent and complex passwords;
- Run anti-malware software to detect whatsoever malicious applications and processes. Just make sure you utilize prophylactic and reliable security software that doesn't rail and gather your data;
- Plow off your mobile information and Wi-Fi when non using them. This might prevent a malicious app from using your data and can disrupt its action if information technology uses online connection;
- Remove the suspicious apps immediately. If your security apps don't find anything, or if y'all don't have any, it's all the same a good thought to delete any apps you downloaded right before the bug started appearing. Check our guidelines on how to remove unwanted apps;
- Inform your friends and contacts and instruct them to ignore suspicious messages coming from you lot;
- Cease broadcasting your personal hotspot when in public equally this makes information technology easier for hackers to breach your device;
- Restore your phone to its factory settings. That might aid if tons of pop-ups or malicious apps have made your phone incommunicable to utilise. This one is a nuclear option, and so use it only as a final resort. Here's how:
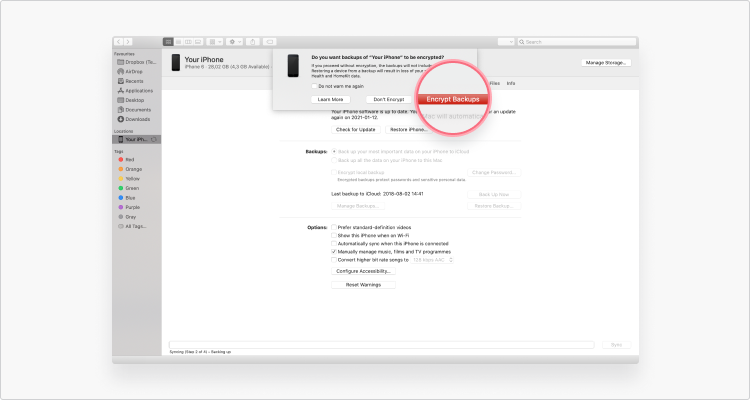
Restoring your iPhone using Catalina
Recall to backup anything important earlier restoring your iPhone to manufacturing plant settings.
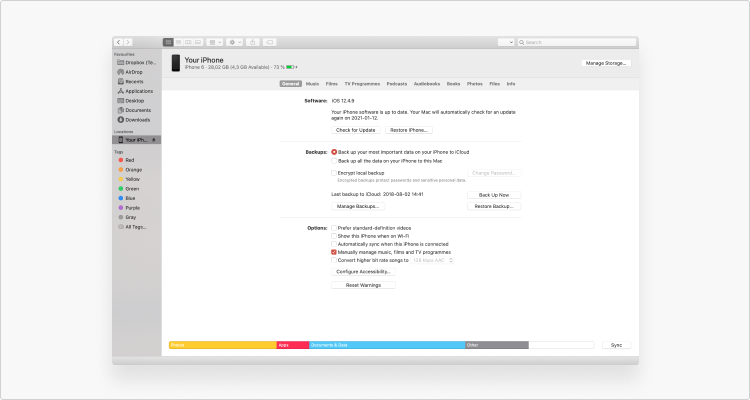
1. On a device with macOS Catalina 10.15.5 or before, connect your telephone to your computer.
2. In the Finder on your mac, select your device in the Finder sidebar.
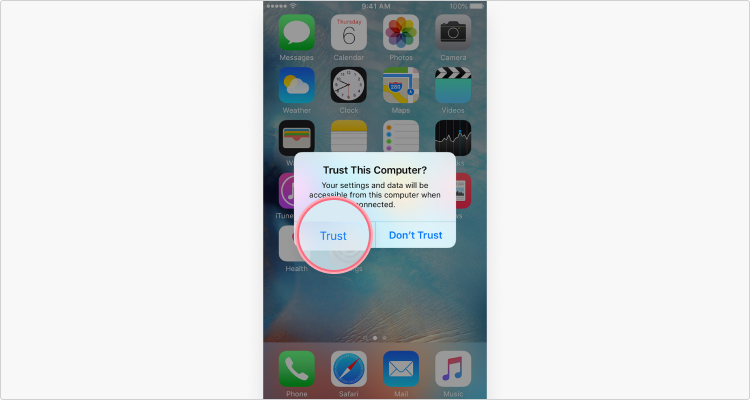
3. Click Trust on your iPhone and enter your passcode.
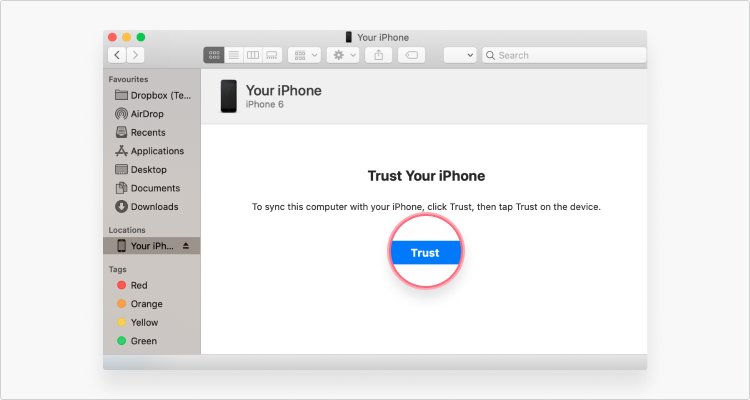
4. Click Restore iPhone
Restoring your Android phone to it's mill settings
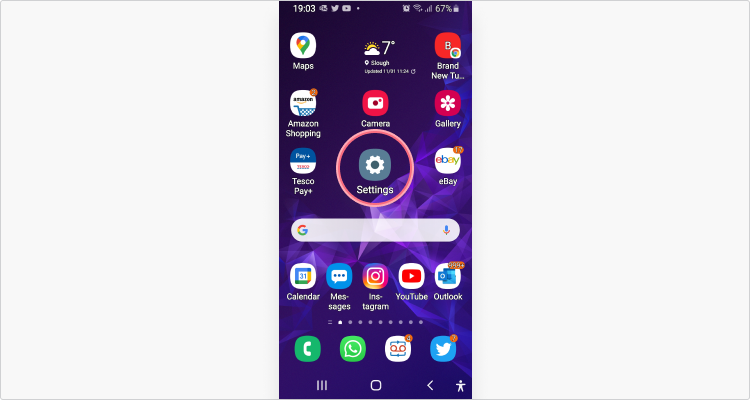
Call back to backup anything important before restoring your Android to factory settings.
1. Open up Settings;
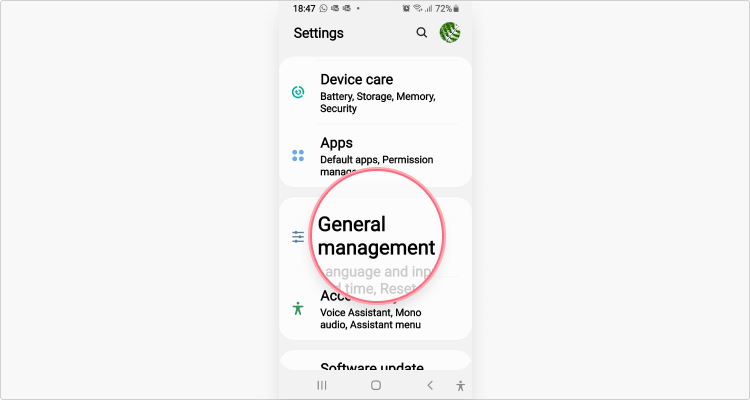
2. Go to General management;
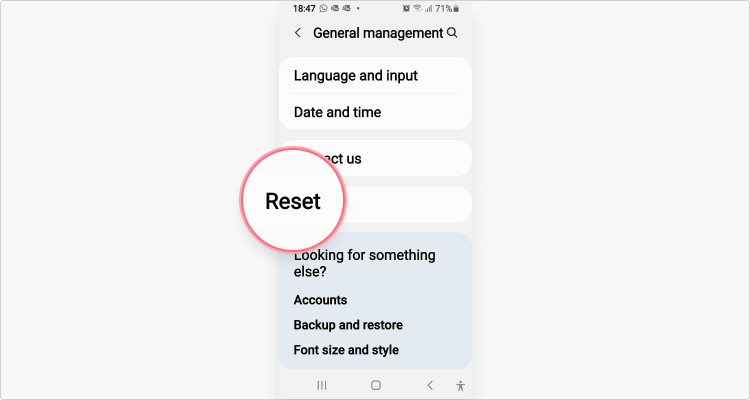
three. Tap Reset;
four. Press Manufactory information reset;
5. Tap Reset.
How to block hackers from my phone
To forbid your phone from being hacked, do the following:
- Turn off your hotspot when in public. If you do need to turn it on, make sure you've made the settings as secure as possible;
- Avoid Wi-Fi or charging spots you don't trust. If you must utilise public Wi-Fi, never exercise and then without a VPN. Also, don't forget to disconnect from public Wi-Fi once you've stopped using it;
- Switch your Bluetooth off when not using it as it can also be an access point for hackers;
- Lock your phone with a password or lock screen;
- Never leave your phone unattended and don't let people you don't know use it;
- Regularly review what apps your phone has to encounter if there are any you don't recognize;
- Practise non open suspicious messages, links, or files. They can be malware or spyware in disguise;
- Install anti-malware apps and constantly update your software;
- Use a VPN for iOS or Android phones to protect your online traffic and browse safely and privately.
- Exercise not employ sites you don't trust. They are a potential source of malware.
Can a phone exist hacked while turned off?
By and large, hackers need to establish an online connection with your telephone to proceeds remote control, and this won't exist active while your device is turned off. However, turning your telephone off doesn't necessarily hateful that information technology'due south in a 'safe-state', some hacks may persist even afterward its turned on again; an extra mic or a photographic camera can exist hidden in the hardware for example, which is why you're asked to leave your phone outside when visiting government intelligence or military machine buildings.
Your phone might non exist hacked while it's off, only that doesn't mean it'south totally condom. Theoretically, there are three ways hackers could assail you while your device is off:
1. If it was jailbroken: the person who jailbroke your phone could have installed all sorts of malicious bugs on it, like tracking software, spyware or malware. While your telephone would have had to be on to be jailbroken, the malware would persist even after you plow your phone on again.
2. If your power button is overwritten: Hackers tin overwrite the command for your power button and then it goes into low power style instead of turning off (this would have been initiated while your telephone was on). Suppose you have the bombardment out (hard with iPhones). A tiny hardware capacitor (a device that stores electric energy) can exist installed on your phone giving it a small charge to let all kinds of malicious things keep, even though you think your phone is off. While this hack would accept been initiated while your phone was on, it overrides the assumption that your phone is in a safe-land, since you lot didn't really turn it off, even though you think yous did.
3. If your number is ported: Technically, this isn't a device-hack, but this is something a hacker could do, even if your phone is off: Hackers tin can steal whatever mobile number and utilize information technology as their ain, by contacting your provider and requesting a number transfer from an old phone to a new one. With a footling social engineering they tin can first hijacking your accounts i past one, by having a password reset sent to your telephone, or by tricking your bank into thinking they're you lot when they call customer service. Sometimes, all they demand to pass security is your SSN, birthdate or address which they can easily find online with enough diligence – in which case it won't brand a divergence if your phone is on or off.
Tin hackers hack your phone past calling you?
No, not direct. A hacker can call you lot, pretending to be someone official, and so proceeds access to your personal details. Armed with that information, they could begin hacking your accounts. But they tin't break into your phone's software and alter it through phone calls lonely.
That being said, your phone can be hacked through advice apps with poor security. In 2019 hackers compromised a smartphone with a single WhatsApp telephone phone call. A WhatsApp VOIP vulnerability allowed criminals to manipulate the device and steal data, private messages, and location details. Zero-day bugs or telephone-telephone call bugs like these tin happen on whatsoever platform, and their remedy really does depend on how quickly developers patch the security flaws.
Is there an app to see if your phone has been hacked?
There are security apps that notify you of unusual activity and ensure you're making use of bones security features similar Screen Lock, Face/Bear on ID and 2FA. They also offering you tips and tricks to boost your phone security, like periodically rebooting your phone.
Specialized spyware apps are also bachelor; these programs can trawl your telephone for subconscious malware and help y'all identify hacks early. Merely the truth is, proactive prevention is improve than trying to counter an attack later information technology'south occurred. Always update your phone and apps to the latest version, ensuring that you go new security patches in real-time. Use an encrypted password manager to generate stiff login credentials, and lock apps individually in case someone cracks your phone'southward passcode. In a higher place all, do your own research regularly, and so you lot can choose the well-nigh reputable and trustworthy security apps available.
Browsing privately with a VPN
Using a VPN while connected to the net is vital to staying away from trouble. Information technology masks your IP address and encrypts your traffic, thus enhancing your privacy and security. Since hackers won't be able to identify y'all online and monitor what you lot're doing on your smartphone, they volition have fewer ways to harm you lot.
VPN is also useful if you lot use public Wi-Fis, which are non always safe. It encrypts your traffic and you tin browse safely wherever you are.
But don't exist enticed by complimentary VPNs, equally they unremarkably accept a subconscious agenda behind their gratis services. Well-nigh free VPN services may collect your data, use it for marketing purposes or even pass it to 3rd parties.
NordVPN is an easy-to-apply app designed for both novice and expert users. Not only does information technology provide you lot with top-notch encryption, but likewise blocks suspicious ads and pop-ups, which are a common way to distribute malware. NordVPN also has the KillSwitch office, which will disconnect you from the web in case you lose a VPN connection. Moreover, a unmarried NordVPN account allows yous to protect up to vi devices, and then you could take your entire household protected.
If yous're looking to plough your smartphone into a fortress, a VPN service is the answer.
Online security starts with a click.
Stay safe with the world's leading VPN
Source: https://nordvpn.com/blog/how-to-tell-if-your-phone-is-hacked/
0 Response to "How to Know if You Iphone Is Hacked"
Post a Comment